As inbox providers work to differentiate legitimate senders and spammers from the billions of messages they receive on a daily basis, marketers are often caught in the crossfire.
As the volume of malicious email grows, it’s essential to make every effort to help inbox providers easily recognize your business as a legitimate sender.
To do this, we rely on email authentication—a crucial factor in deliverability and fraud prevention.
The two most common methods for authenticating emails are Sender Policy Framework (SPF) and Domainkeys Identified Mail (DKIM). When authentication fails under one of these methods, a domain’s Domain-based Message Authentication, Reporting, and Conformance (DMARC) policy is checked to see what to do next with that message.
Since its release, DMARC has been considered a best practice, but not a necessity for bulk email senders. Now, that’s all changing. Because senders who don’t have DMARC policies are much more likely to be spammers, Google and Yahoo’s new sender requirements are collectively shifting the industry standard from best practice to absolute necessity.
No DMARC policy, no entry into the inbox.
In other words, if your emails aren’t authenticated and they fail to pass a DMARC check, they won’t land in your audience’s inboxes. As of April 1, 2024, these messages will be rejected and bounce completely from Yahoo or Google email inboxes.
Why is DMARC important?
DMARC is considered an industry best practice when protecting:
- Your brand and domain name
- Your sending reputation, which is key for email deliverability
Think of it this way: Most marketers spend significant time and money building a brand their customers can trust. Email is part of that process. If a customer receives spam or malicious email on behalf of a brand they have done business with, this may compromise their trust in that brand and even end that relationship.
Even worse, imagine a third party sends an email using your hard-earned reputation for a malicious purpose, like stealing someone’s identity or personal information. The consequences could extend beyond eroding trust and end up causing permanent damage to your brand’s image.
How does DMARC work?
DMARC is essentially your domain/brand’s email reputation guard dog. Its purpose is to prevent unauthorized sources from sending email on your behalf (a practice also known as spoofing) for malicious purposes, such as phishing scams.
Here’s how the DMARC authentication process works:
- Alignment: DMARC passes or fails a message based on how close the message “from” header matches the sending domain specified by either SPF or DKIM.
- Policy enforcement: DMARC instructs mail servers on what to do with the message if it fails DMARC checks, defined by one of 3 possible settings:
p=none: place the message in the inbox at your own riskp=quarantine: do not place the message in the inbox; place it in spam/junkp=reject: do not accept the message; it is likely not from the owner of the domain the email originated from, and should be bounced- p=none: place the message in the inbox at your own risk
- p=quarantine: do not place the message in the inbox; place it in spam/junk
- p=reject: do not accept the message; it is likely not from the owner of the domain the email originated from, and should be bounced
- Audit mail traffic: Your DMARC record can be configured to provide reporting on who or what is sending messages on your domain’s behalf. Third-party tools like EasyDMARC or Dmarcian can manage this process to secure your domains as needed. If someone is attempting to spoof your emails or is sending unauthorized emails (like a non-customer facing department), you can identify those sources and prevent them from sending further emails.
What led to the creation of DMARC?
Prior to the adoption of DMARC in 2013, the authentication methods the policy uses already existed.
SPF has been around, in some form, since 2000 or so. DKIM came on the scene a few years later, around 2004, for a number of major players—most notably, Yahoo and Cisco Systems.
Let’s take a closer look at SPF and DKIM to see how they work.
Sender Policy Framework (SPF)
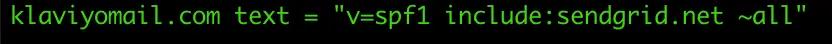
SPF is used to authenticate the sender of an email. With an SPF record in place, inbox providers can verify that a mail server is authorized to send email for a specific domain. The SPF record resides in the DNS TXT record and contains a list of IP addresses that are allowed to send email on behalf of your domain.
An SPF record starts with “v=spf1”. For example, if you do a TXT lookup for “klaviyomail.com”, you will find an entry like this:
DomainKeys Identified Mail (DKIM)
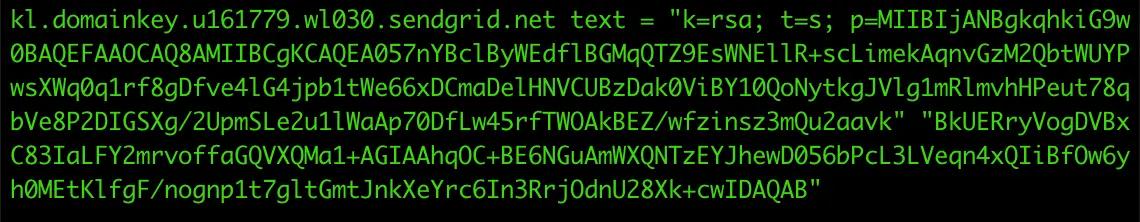
DKIM is used to verify the authenticity of a message by using a cryptographic signature which is encrypted and added to the header of the message. When the message is received, a public key found in the DKIM record of the sending domain’s DNS is used to decrypt the DKIM signature and authenticate the message.
A DKIM record resides in a special location under the TXT records. In our example, you can find the DKIM record under the “kl._domainkey” subdomain:
How to authenticate with DMARC
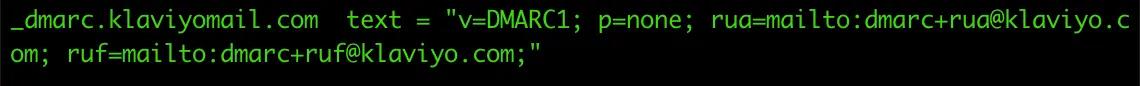
A DMARC record shows up within the TXT records of the _dmarc subdomain and starts with “v=DMARC1;”.
For example, if you do a TXT lookup for “_dmarc.klaviyomail.com”, you will find an entry like this:
There are different steps for authenticating DMARC, though, depending on the DNS host. Find specific instructions based on your DNS host here.
Why DMARC is now table stakes for marketers
The world of email is quickly moving to a place where no authentication effectively guarantees your message will be rejected.
At Klaviyo, in line with industry best practices, all senders must implement SPF, DKIM, and DMARC records. This, in turn, equips senders with the technical set-up necessary for meeting the recent requirements outlined by Yahoo and Gmail—which means you can rest easy, and focus on other areas of deliverability and marketing best practices.
All Klaviyo customers, large and small, should have a DMARC policy for their brand’s domain. Even if you are not sending enough email to be classified as a “bulk sender” under Yahoo and Google’s new sender requirements, your business is growing—and it’s best to be prepared ahead of time.
Do your future business a favor and get started with DMARC now.
Related content
- Understanding email authentication
- Your complete guide to email deliverability: avoid the spam folder for maximum engagement
- Google + Yahoo’s new sender requirements: how to optimize your strategy
- BIMI: the untapped tool for email marketers
Power smarter digital relationships with Klaviyo SMS.
Get started